





























IT, Knowledge, Entertainment, Fun etc.

Yes you can, by using the Windows Server 2003 Active Directory Domain Rename Tools.
If you've installed Exchange 2000 into the forest before running ADPrep, you have to correct some mistakes that were made in the Exchange 2000 schema extensions.
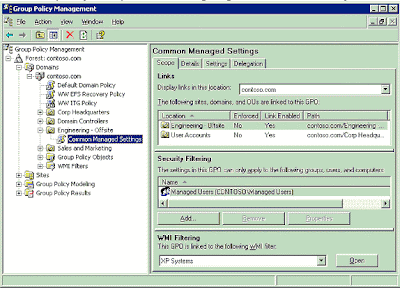
Group Policy is a powerful tool for managing the Windows 2000 (and later) environment. The value of Group Policy can only be realized through properly applying the GPOs to the Active Directory containers you want to manage. Determining which users and computers will receive the settings in a GPO is referred to as “scoping the GPO”. Scoping a GPO is based on three factors:
GPMC exposes features that are available in the underlying operating system. Because new features have been added to Group Policy since Windows 2000, certain features will only be available in GPMC depending on the operating system that has been deployed on the domain controllers and clients. This section describes these dependencies. In general, there are four key issues that determine whether a feature is available in GPMC:


How can I manage my Exchange 2003 server from a Windows XP/2000/2003 workstation?


Download Exchange 2003 SP2 (109mb)![]()
street bike tricks
Yaaro :
The pen of the future will use inkjet technology to deliver a multitude of colours from its tip, according to recent filings from prolific patenter Silverbrook Research in Balmain, Australia.
Preface:
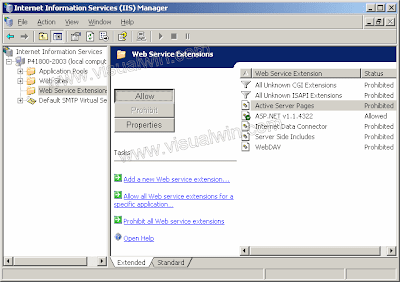
Windows Server 2003 includes a new default security configuration for Internet Explorer, called Internet Explorer Enhanced Security Configuration (ESC). ESC impacts the Security Zones and Privacy settings within the Internet Explorer Maintenance settings of a GPO. The Security Zones and Privacy settings can either be ESC enabled or not.
Group Policy can be applied to users and computers at a site, domain, or OU. GPOs from parent containers are inherited by default. When multiple GPOs apply to these users and computers, the settings in the GPOs are aggregated. For most policy settings, the final value of a given policy setting is set only by the highest precedent GPO that contains that setting. (However, the final value for a few settings will actually be the combination of values across GPOs.) Precedence of GPOs determined by the order of processing for the GPOs. GPOs processed last have highest precedence. GPOs follow the SDOU rule for processing; site first, then domain and followed by OU including nested OUs. A nested OU is one that has another OU as its parent. In the case of nested OUs, GPOs associated with parent OUs are processed prior to GPOs associated with child OUs. In this processing order, sites are applied first but have the least precedence. OUs are processed last and have the highest precedence.

!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
How to look Happy at work
As of today all personnel will be expected to look happy at work. Rubber bands and paper clips will be provided at no cost .
* Workload getting to you?
* Feeling stressed?
* Too many Priority 1 assignments?
Here is the new low cost way to cope with multiple Priority 1 assignments!
Take 2 paperclips and rubber bands. Fig 1
Assemble them as shown on the picture. Fig. 2
Apply as shown in fig 3.
Enjoy your day.
This new office equipment will help you to reach the end of the day
with a smile on your face!
The Intel® Xeon® processor 7400 series, offers the industry's highest virtualization performance so you can do more with less. With key platform innovations built-in, the Intel® Xeon® processor 7400 series offers more headroom, reliability, and the highest expandability for large-scale server consolidation.


If you also have NAT installed on the same server that hosts the DNS server, you will get these errors. NAT has a DNS Proxy setting that enables DHCP clients to direct DNS queries to the NAT server. The client DNS queries are then forwarded to the NAT server's configured DNS server. The DNS Proxy and the DNS Server service cannot coexist on the same host, if the host is using the same interface and IP address with the default settings.
To workaround this issue, use one of the following three methods:
Install NAT and DNS on different servers.
Use the DHCP server Service in NAT, NOT the DHCP Allocator and DNS Proxy.
Set the DNS Server so it doesn't listen on the IP address of the NAT private interface:
In the DNS MMC snap-in, right click the DNS server and press Properties.
In the Listen on section of the Interfaces tab, select the Only the following IP addresses check box.
Select the IP address that you do NOT want the DNS server to listen on, and press Remove. DNS will NOT respond to queries that are directed to this removed address.
Press OK and close the snap-in.
This article discusses how to upgrade Microsoft Windows 2000 domain controllers to Microsoft Windows Server 2003 and how to add new Windows Server 2003 domain controllers to Windows 2000 domains.
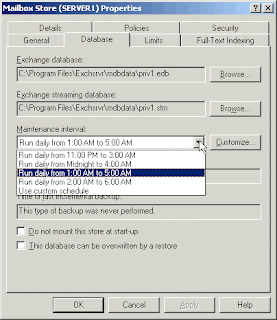
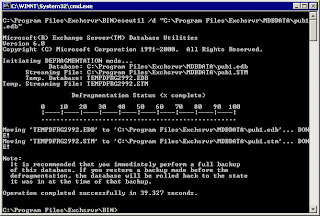
Exchange databases run a defragmentation process once a day by default. This process rearranges mailbox store and public folder store data more efficiently, eliminating unused storage space. Exchange database online defragmentation occurs automatically as part of the database maintenance process. Online defragmenting is performed automatically at 2:00 AM every day by default. Online defragmentation makes additional database space available by detecting and removing database objects that are no longer being used. The defragmentation process provides more database space without actually changing the file size of the database.
Security Configuration and Analysis is a tool for analyzing and configuring local system security.
The state of the operating system and applications on a computer is dynamic. For example, security levels may be required to change temporarily to enable immediate resolution of an administration or network issue; this change can often go unreversed. This means that a computer may no longer meet the requirements for enterprise security.
Regular analysis enables an administrator to track and ensure an adequate level of security on each computer as part of an enterprise risk management program. Analysis is highly specified, information about all system aspects related to security is provided in the results. This enables an administrator to tune the security levels, and most importantly, detect any security flaws that may occur in the system over time.
Security Configuration and Analysis enables quick review of security analysis results: recommendations are presented alongside current system settings, and icons or remarks are used to highlight any areas where the current settings do not match the proposed level of security. Security Configuration and Analysis also offers the ability to resolve any discrepancies revealed by analysis.
If frequent analysis of a large number of computers is required, as in a domain-based infrastructure, the Secedit.exe command line tool may be used as a method of batch analysis. However, analysis results still must be viewed using Security Configuration and Analysis. For more information, see Automating security configuration tasks
This tool can also be used to directly configure local system security. Through its use of personal databases, you can import security templates created with the Security Templates snap-in, and apply these templates to the Group Policy object for the local computer. This immediately configures the system security with the levels specified in the template. For more information, see Managing Security Templates